Oracle and Devoxx4Kids worked together to provide a fun and technology-rich experience for kids at JavaOne 2014. Inspirational, rewarding, and fun are three words that summarize the event for me. If you live in/around San Francisco Bay Area, then highly recommend joining meetup.com/Devoxx4Kids-BayArea/ for a continued experience!
136 kids attended the event and their age/gender are shown below:
Overall, the instructors seem to have done a good job:
The event itself was well rated:
Minecraft Modding continues to be the top rated workshop:
Here are some pictures from the event:
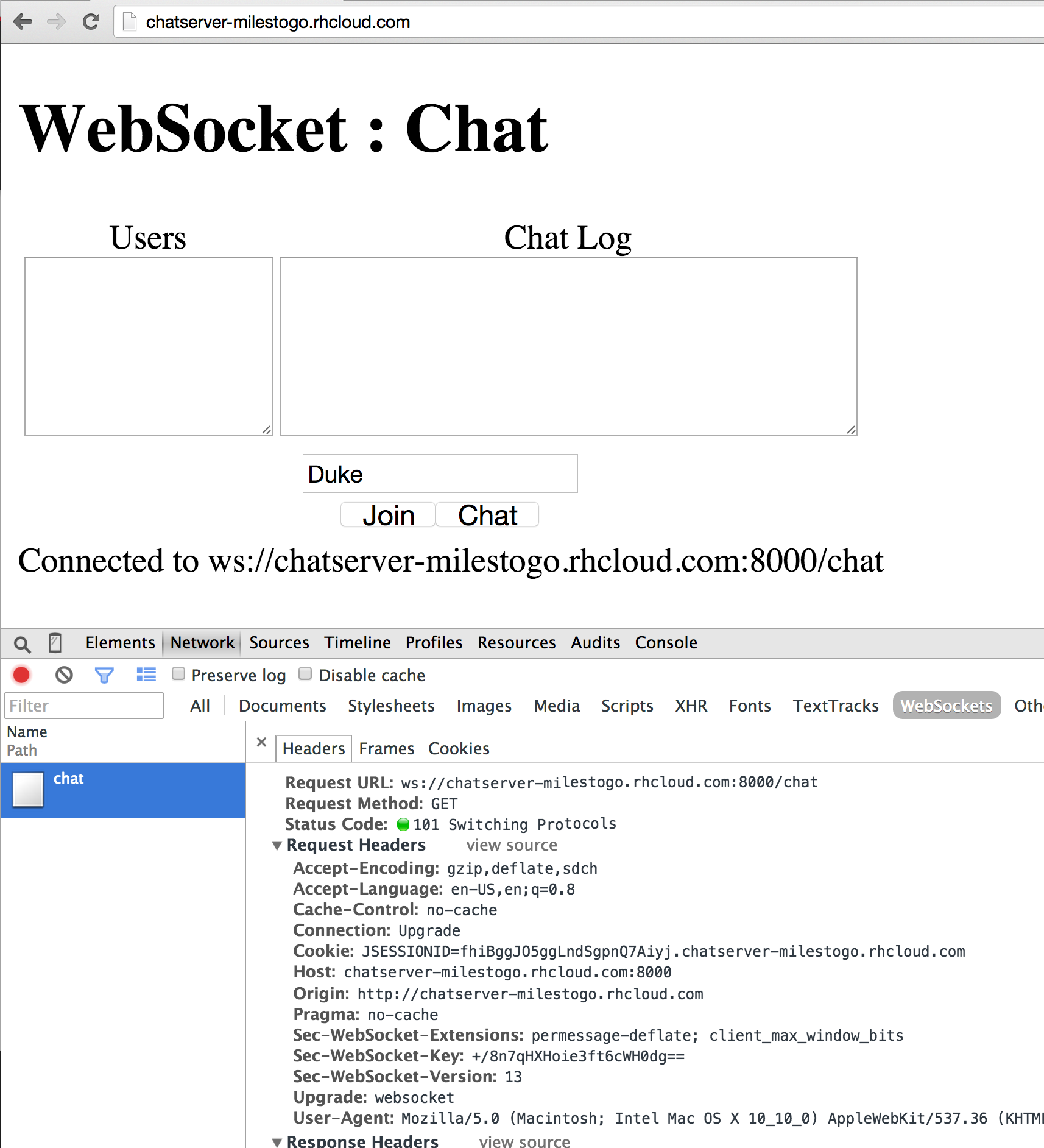
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
Check out the complete album:

Picture is worth a thousand words, a video is worth a million words. Check out kids in action (thanks to @Oraclejavamag for the video):
Here is another wonderful video created (@BertBreeman):
It takes a village to run an event like this. This was certainly not possible without the impeccable support from Oracle team, JUG leaders, Java Champions, and several other volunteers who helped us through out the team!
This summarizes the event for me:
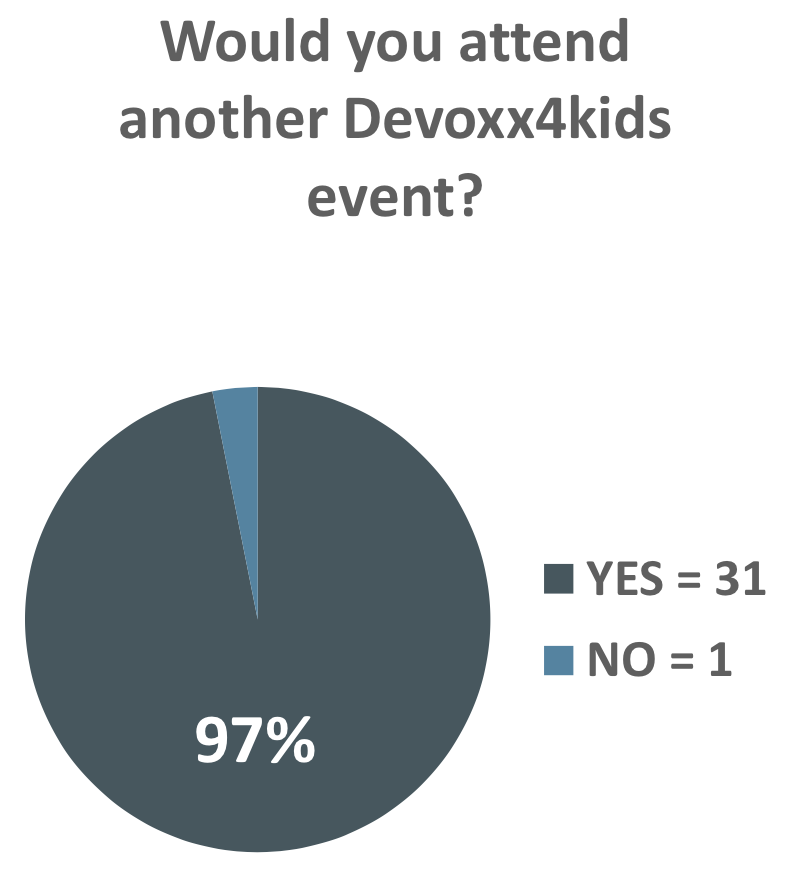
I’d like to know if that one NO was an accidental one 😉