- It’s a space to share ideas – whether that means submitting articles, tutorials, or blog posts, or telling the Voxxed editorial team about some news or ideas you’ve got that you’d like them to broadcast on your behalf to the whole community.
- “Devoxx everyday,” bringing together the best of the conversation from the Java ecosystem into one portal.
- A place to facilitate discussion and wider learning with curated links to wider Parleys presentations and interviews.
- A new kind of media portal which will be hugely influenced by the community that uses it.
Stephan Janssen (@stephan007), the serial entrepreneur and the man behind Devoxx had to say the following about this initiative:
The Voxxed story starts with Devoxx, which I started in part so that I could get my personal fix of the best tech content around. I’m proud of how important Devoxx has become for developers in this community, but it only happens a few times a year. Where can I go then for a daily community hit, especially with online media so fragmented? So I thought, let’s bring everything together by pulling in blog feeds, reporting news, and housing tutorials, presentations and training courses – everything that people share that makes Devoxx what it is, into one place
There are so many people out there with amazing tech know-how that fly under the radar. I hope Voxxed can be the place where they share their stories. It’s also somewhere for new talent to shine. The Rockstars of our sector probably had their first speaking gig at a local community event. But not everyone enjoys the sometimes terrifying arena of a few hundred people staring back at them. By letting the community publish online, Voxxed gives new voices a platform. Today is just the first stage – a site that looks good, is easy to use and has great content. The next stage is for the community to drive it with excellent content and ideas”
Lucy Carey (@Lucyrushi), editor of Voxxed, says:
I love the creativity and energy of the tech sector, and one of the best parts of my job is being able to share stories from the people behind all the exciting stuff that this huge community is generating. When I heard that there was an opportunity to get involved with a new site developed by the people behind Parleys and Devoxx, I was hugely keen to come on board.
I’m proud and excited to be part of the inaugural launch of voxxed.com with a video course on Learning Java EE 7 Essentials, check out a preview:
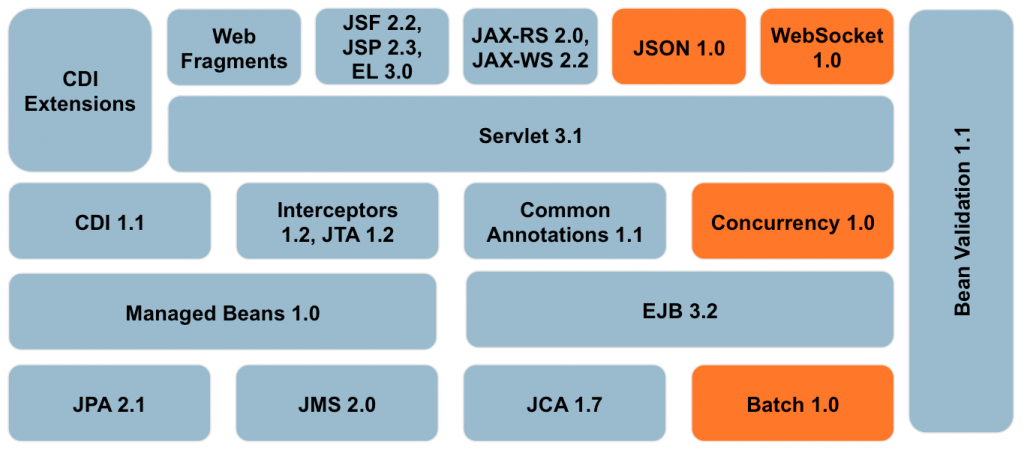
The first version of this course provide introduction to the following Java EE 7 technologies:
- Java API for WebSocket (JSR 356)
- Java API for JSON Processing (JSR 353)
- Batch Processing for the Java Platform (JSR 352)
- Concurrency Utilities for Java EE (JSR 353)
- Java API for RESTful Services (JSR 339)
- Java Message Service (JSR 343)
- Contexts & Dependency Injection (JSR 346)
The four new technologies in the course, WebSocket, JSON-P, Batch, and Concurrency, are explained in detail. Key features of JAX-RS 2.0, JMS 2.0, and CDI 1.1 are explained in detail, with a clearly marked emphasis on new features added in Java EE 7.
This is purely a technology-focused course. So whether you are using WildFly, GlassFish, or TmaxSoft JEUS today or will be using JBoss EAP 7+, WebLogic 12.1.4+, WebSphere Liberty Profile or any other Java EE 7 compliant application server, this course would be a great way to understand the key concepts of technology.It discusses the patterns and anti-patterns of different technologies using code-extensive slides.
Buy the course here!
If your team is embarking on a new project that uses Java EE 7 technology, this course will server as a great introduction as well. The usual benefits of parleys.com such as offline viewing, synchronized slides + video, ability to skip slides etc are all available as well.
Future additions planned for this course are:
- JavaServer Faces (JSR 344)
- Java Servlets (JSR 340)
- Java API for Persistence (JSR 338)
- Enteprise JavaBeans (JSR 345)
- Develop/Deploy/Debug a Java EE 7 Application Eclipse
- Develop/Deploy/Debug a Java EE 7 Application using NetBeans
- Develop/Deploy/Debug a Java EE 7 Application using IntelliJ
- Java EE 7 Development/Deployment on OpenShift
The course is available at an introductory low price of €69.99. Bulk pricing discounts are also available, drop a comment on the blog for that. However this price will increase as more course items are added in the next few weeks. If you purchase the course today, then future updates/additions are free!
So, act now and purchase this course today ![]()
Many thanks to Carlo and rest of the Parleys team for their wonderful support through out the process!