Peter Moskovits from Kaazing (@peterm_kaazing) and I gave a university talk at Devoxx 2014 on Nuts and Bolts of WebSocket. The slides are now available at:
The entire session is recorded and will be made available on parleys.com in the coming weeks/months.
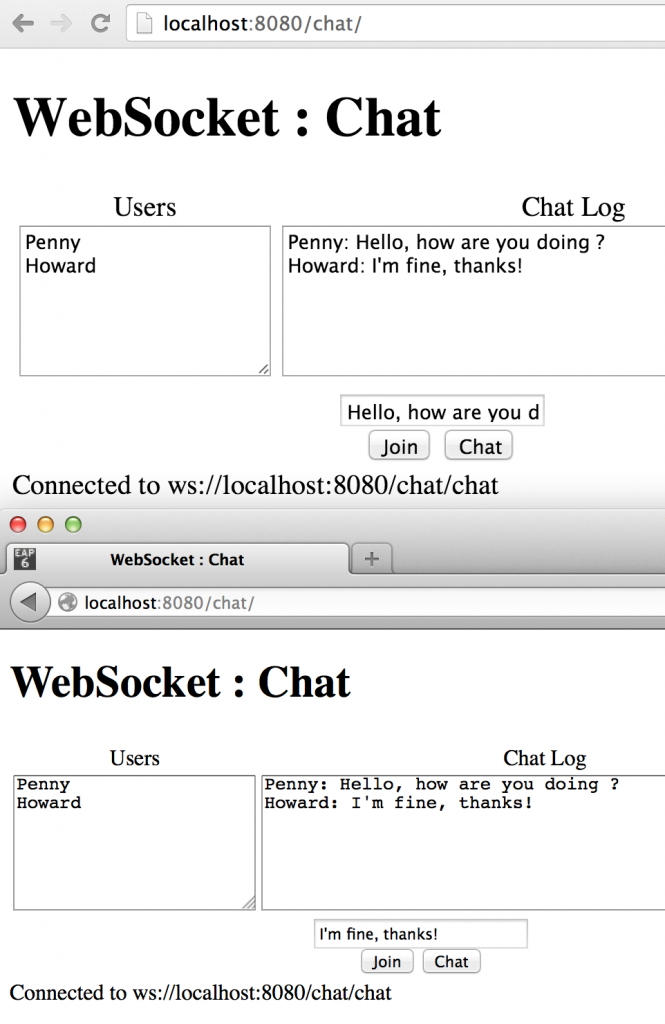
The complete script for the demo is available at github.com/arun-gupta/nuts-and-bolts-of-websocket (including pointers to the demos). Most of the demos are anyway available at the following links:
- Chrome Developer Tools: http://www.websocket.org/echo.html
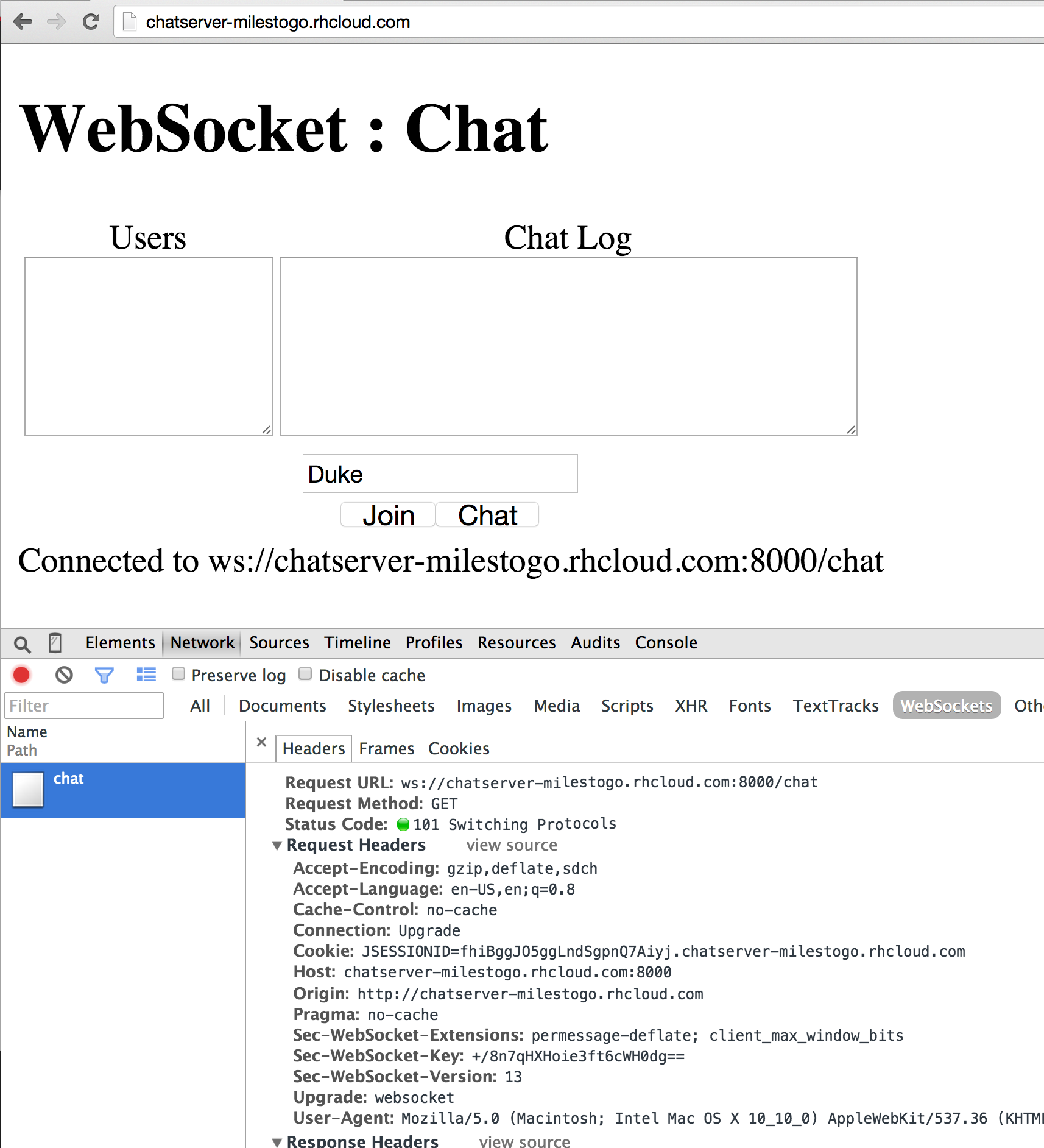
- Canonical Chat Server: https://github.com/javaee-samples/javaee7-samples/tree/master/websocket/chat
- Chat Server on OpenShift: http://blog.arungupta.me/2014/10/websocket-chat-wildfly-openshift-techtip51/
- Collaborative Whiteboard: https://github.com/javaee-samples/javaee7-samples/tree/master/websocket/whiteboard
- WebSocket Client API: https://github.com/javaee-samples/javaee7-samples/tree/master/websocket/google-docs
- User-name based security: http://blog.arungupta.me/2014/10/securing-websockets-username-password-servlet-security-techtip49/
- TLS-based security: http://blog.arungupta.me/2014/10/securing-websocket-wss-https-tls-techtip50/
- Load Balancing WebSocket: http://blog.arungupta.me/2014/08/load-balance-websockets-apache-httpd-techtip48/
- JMS and JavaScript: Pub/Sub over WebSocket: http://demo.kaazing.com/demo/jms/javascript/jms-javascript.html
- STOMP over WebSocket: http://blog.arungupta.me/2014/11/stomp-over-websocket-tech-tip-53/
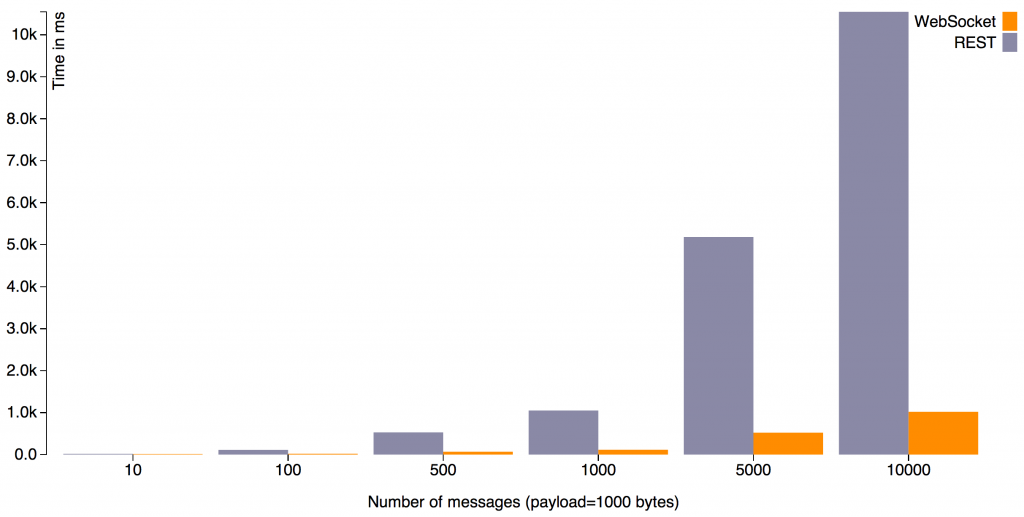
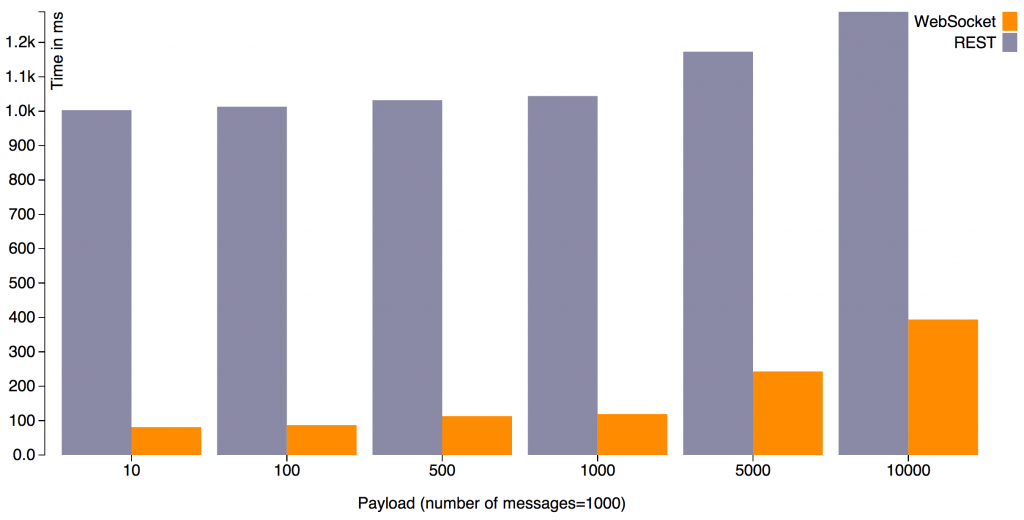
- Compare WebSocket with REST: https://github.com/javaee-samples/javaee7-samples/tree/master/websocket/websocket-vs-rest-payload
Positive feedback from twitter overall:
Nice working application build in seconds! #Devoxx #WebSocket And once again, we developer are very… http://t.co/mLsnKf4Vcp
— Miguel Discart (@Miguel_Discart) November 10, 2014
Who’s doing Nuts and Bolts of #Websocket ? @arungupta #Devoxx pic.twitter.com/nAeGFTj6vx
— Antoine Sabot-Durand (@antoine_sd) November 10, 2014
@arungupta and @peterm_kaazing gave a very informative code live session about #Websocket in #Devoxx
— jianing zhang (@jianinz) November 10, 2014
#Devoxx #websocket really interesting uni session today in Antwerpen. Arun and Peter giving good info
— Koen (@koendroid) November 10, 2014
Nuts and Bolts of #Websocket SRO #Devoxx @arungupta pic.twitter.com/XoedutFiVJ
— Java (@java) November 10, 2014
Really cool WebSocket demo. Open http://t.co/C9ybgFPTLw and control it from mobile. #devoxx #websocket
— DiversIT Europe (@diversit) November 10, 2014
@arungupta & @peterm_kaazing gave amazing talk on #websocket at #devoxx
— Vladimir Milovanović (@mmwlada) November 10, 2014
At #Devoxx I Just developed & deployed my first websocket app on WildfFly on Openshift in 4mins! Thanks @arungupta Great Talk
— Sabri Skhiri (@sskhiri) November 10, 2014
And it was rated the top talk for the day until 6pm:
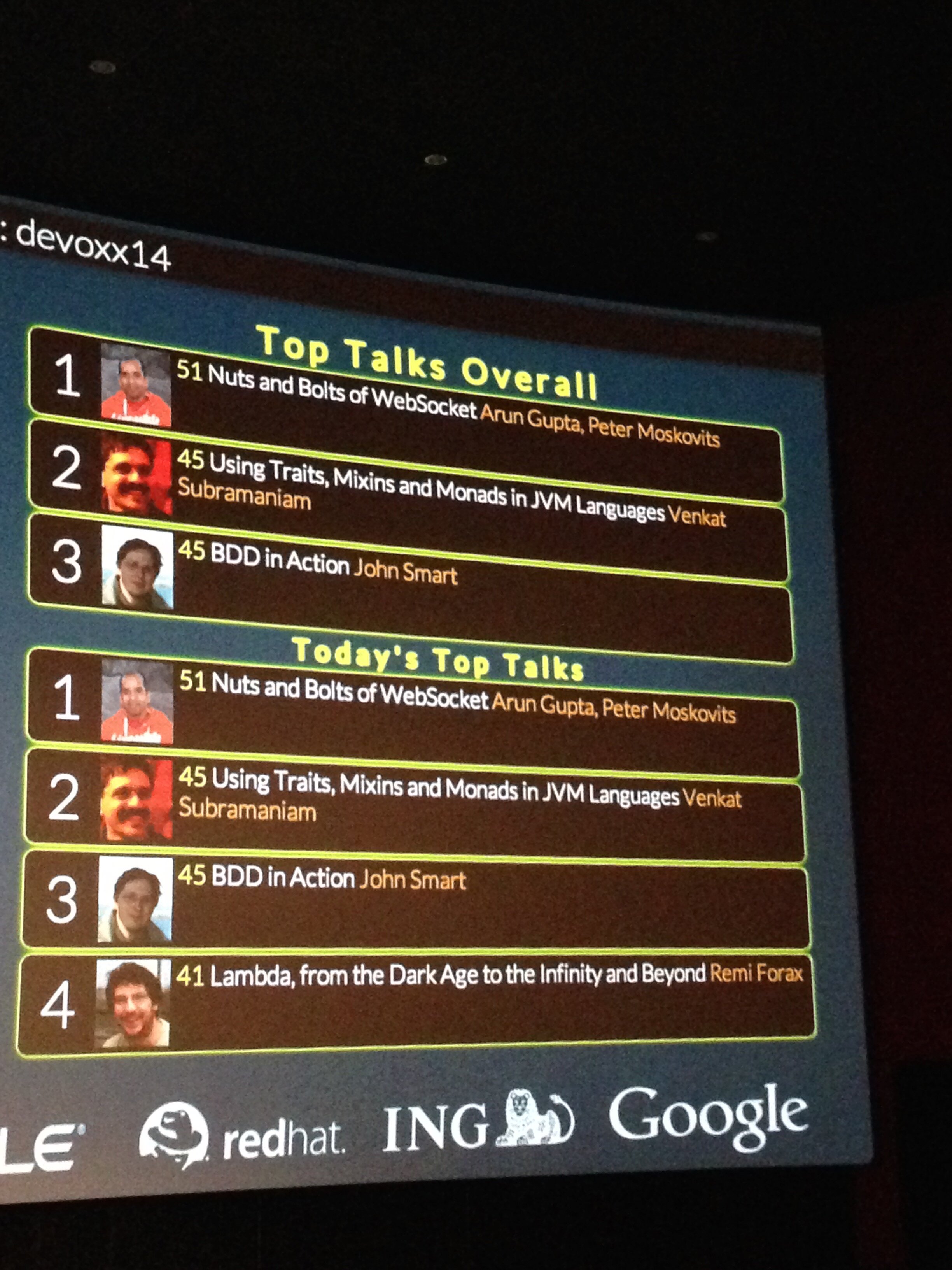
With Red Hat spirit, “the more you share, the more you grow”, share the slides and demos all over and spread the love!
Happy Devoxx!