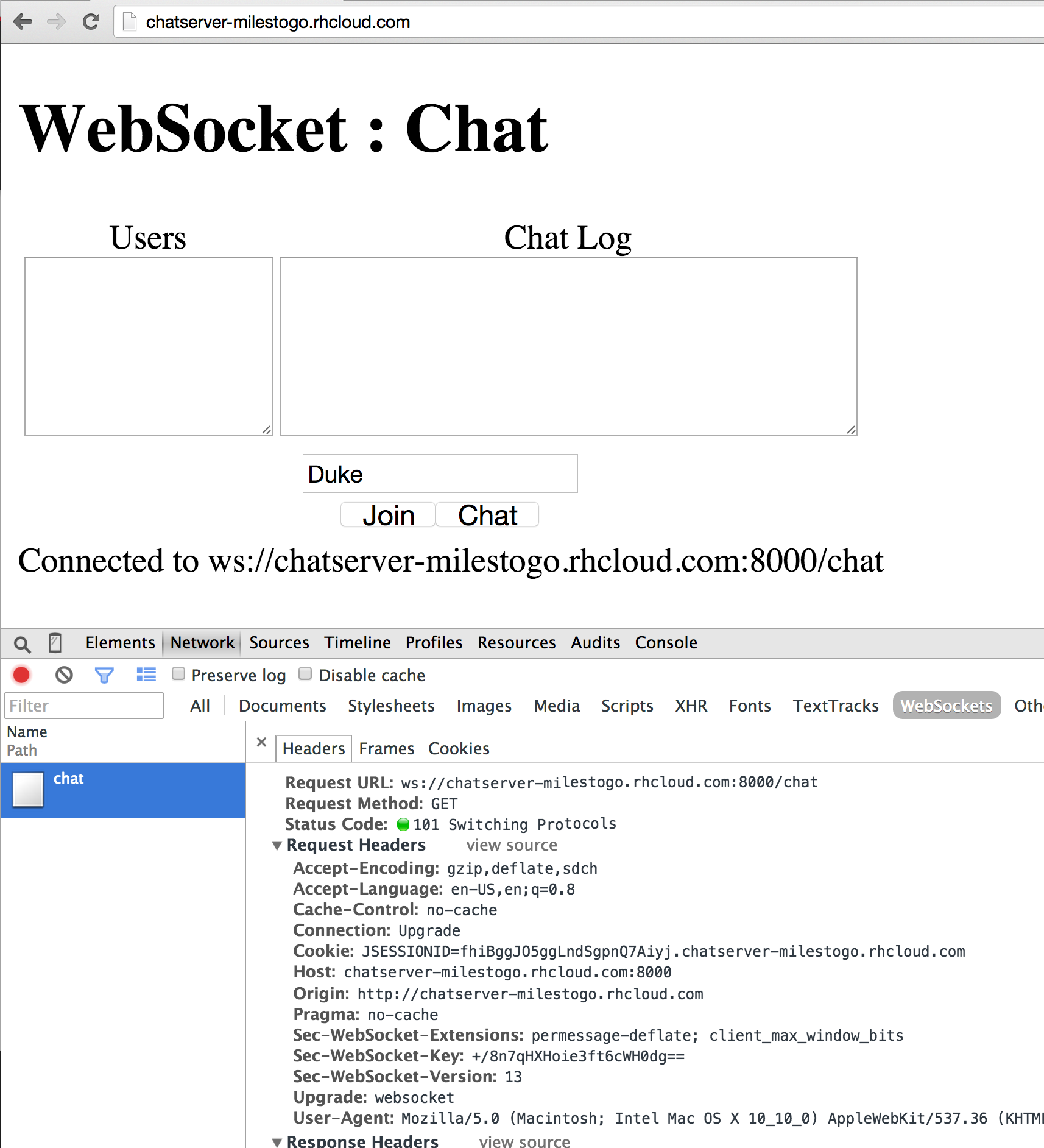
A new instance of WildFly can be easily provisioned on OpenShift by using the quick start. Just a single click, and you are ready to go!
Generally power users of OpenShift use Command Line Tools. However you could not create WildFly cartridge using the CLI tools. But bug# 1134134 is now resolved.
And so now rhc cartridge-list shows:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
workspaces> rhc cartridge-list
jbossas-7 JBoss Application Server 7 web
jboss-dv-6.0.0 (!) JBoss Data Virtualization 6 web
jbosseap-6 (*) JBoss Enterprise Application Platform 6 web
jenkins-1 Jenkins Server web
nodejs-0.10 Node.js 0.10 web
perl-5.10 Perl 5.10 web
php-5.3 PHP 5.3 web
php-5.4 PHP 5.4 web
zend-6.1 PHP 5.4 with Zend Server 6.1 web
python-2.6 Python 2.6 web
python-2.7 Python 2.7 web
python-3.3 Python 3.3 web
ruby-1.8 Ruby 1.8 web
ruby-1.9 Ruby 1.9 web
ruby-2.0 Ruby 2.0 web
jbossews-1.0 Tomcat 6 (JBoss EWS 1.0) web
jbossews-2.0 Tomcat 7 (JBoss EWS 2.0) web
jboss-vertx-2.1 (!) Vert.x 2.1 web
<strong>jboss-wildfly-8 (!) WildFly Application Server 8.1.0.Final web</strong>
diy-0.1 Do-It-Yourself 0.1 web
10gen-mms-agent-0.1 10gen Mongo Monitoring Service Agent addon
cron-1.4 Cron 1.4 addon
jenkins-client-1 Jenkins Client addon
mongodb-2.4 MongoDB 2.4 addon
mysql-5.1 MySQL 5.1 addon
mysql-5.5 MySQL 5.5 addon
phpmyadmin-4 phpMyAdmin 4.0 addon
postgresql-8.4 PostgreSQL 8.4 addon
postgresql-9.2 PostgreSQL 9.2 addon
rockmongo-1.1 RockMongo 1.1 addon
switchyard-0 SwitchYard 0.8.0 addon
haproxy-1.4 Web Load Balancer addon
Note: Web cartridges can only be added to new applications.
(*) denotes a cartridge with additional usage costs.
(!) denotes a cartridge that will not receive automatic security updates.
|
The newly added cartridge of WildFly 8 is shown in bold.
And so now a new WildFly instance can be easily provisioned using the CLI as:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
workspaces> rhc app-create mywildfly jboss-wildfly-8
Application Options
-------------------
Domain: milestogo
Cartridges: jboss-wildfly-8
Gear Size: default
Scaling: no
Creating application 'mywildfly' ... Artifacts deployed: ./ROOT.war
done
WildFly 8 administrator added. Please make note of these credentials:
Username: adminLWEMEdW
Password: 9u6jpWuQU6hg
run 'rhc port-forward mywildfly' to access the web admin area on port 9990.
Waiting for your DNS name to be available ... done
Cloning into 'mywildfly'...
Warning: Permanently added the RSA host key for IP address '54.163.104.22' to the list of known hosts.
Your application 'mywildfly' is now available.
URL: http://mywildfly-milestogo.rhcloud.com/
SSH to: 545ac1d0e0b8cd8ad800018d@mywildfly-milestogo.rhcloud.com
Cloned to: /Users/arungupta/workspaces/mywildfly
Run 'rhc show-app mywildfly' for more details about your app.
|
And then the application’s main page is accessible as shown:
And the application can be deleted as:
|
1
2
3
4
5
6
7
8
|
workspaces> rhc app-delete mywildfly
This is a non-reversible action! Your application code and data will be permanently deleted if you continue!
Are you sure you want to delete the application 'mywildfly'? (yes|no): yes
Deleting application 'mywildfly' ... deleted
|
Simple, isn’t it ?
See several other OpenShift getting-started related blog entries here.