Tech Tip #57 explained how to create your own Docker images. That particular blog specifically showed how to build your own WildFly Docker images on CentOS and Ubuntu. Now you are ready to share your images with rest of the world. That’s where Docker Hub comes in handy.
Docker Hub is the “distribution component” of Docker, or a place to store and search images. From the Getting Started with Docker Hub docs …
The Docker Hub is a centralized resource for working with Docker and its components. Docker Hub helps you collaborate with colleagues and get the most out of Docker.
Starting and pushing images to with Docker Hub is pretty straight forward.
- Pushing images to Docker Hub require an account. It can be created as explained here. Or rather easily by using
docker logincommand.
1234567wildfly-centos> docker loginUsername: arunguptaPassword:Email: arun.gupta@gmail.comLogin Succeeded
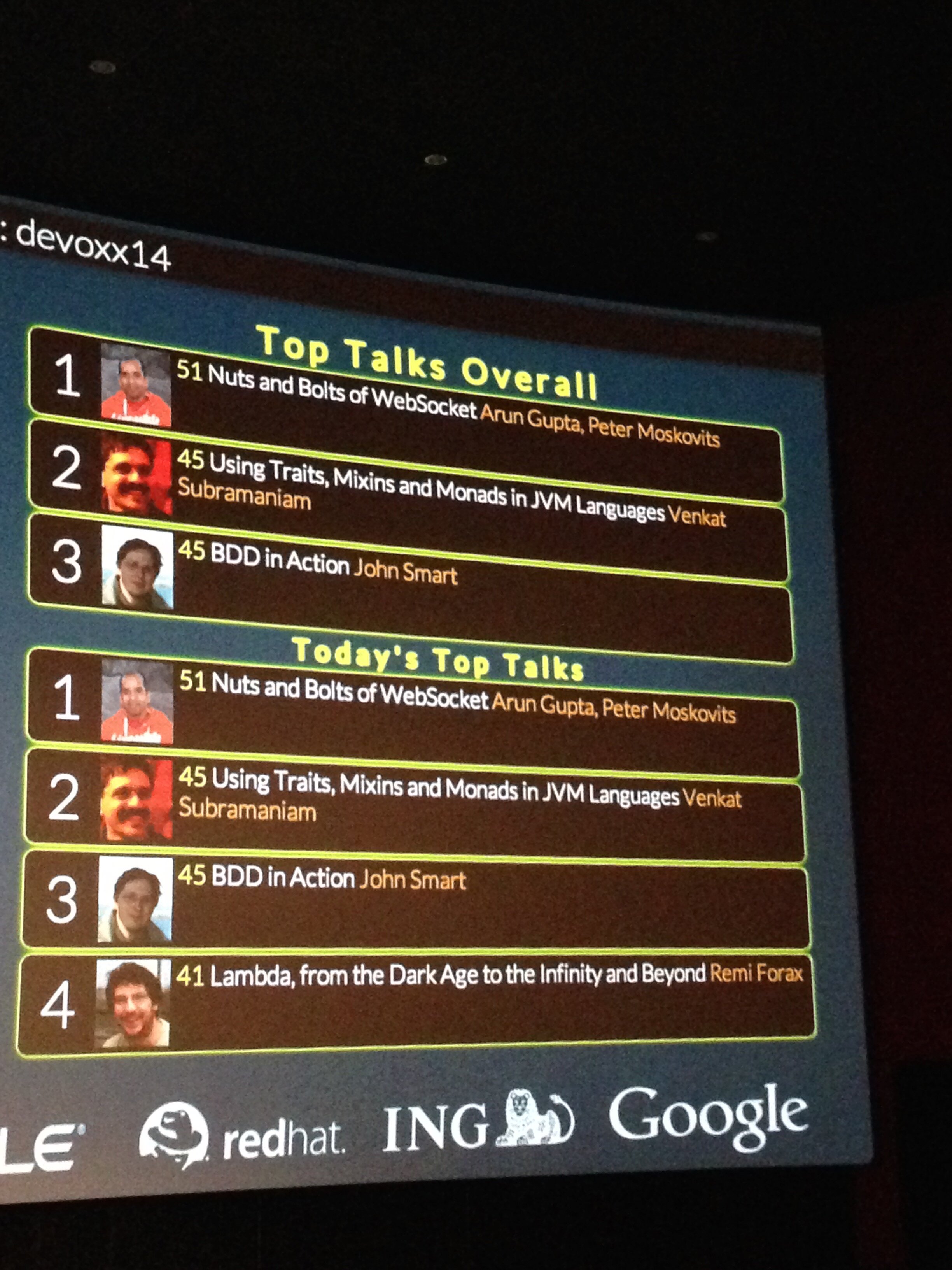
Searching on WildFly shows there are 72 images:
1234567891011121314151617181920212223242526272829303132333435363738394041424344454647484950515253545556575859606162636465666768697071727374wildfly-centos> docker search wildflyNAME DESCRIPTION STARS OFFICIAL AUTOMATEDjboss/wildfly WildFly application server image 42 [OK]sewatech/wildfly Debian + WildFly 8.1.0.Final with OpenJDK ... 1 [OK]kamcord/wildfly 1openshift/wildfly-8-centos 1 [OK]abstractj/wildfly AeroGear Wildfly Docker image 1jsightler/wildfly_nightly Nightly build from wildfly's github master... 1centos/wildfly CentOS based WildFly Docker image 1aerogear/unifiedpush-wildfly 1 [OK]t0nyhays/wildfly 1 [OK]tsuckow/wildfly-propeller Dockerization of my application *Propeller... 0 [OK]n3ziniuka5/wildfly 0 [OK]snasello/wildfly 0 [OK]jboss/keycloak-adapter-wildfly 0 [OK]emsouza/wildfly 0 [OK]sillenttroll/wildfly-java-8 WildFly container with java 8 0 [OK]jboss/switchyard-wildfly 0 [OK]n3ziniuka5/wildfly-jrebel 0 [OK]dfranssen/docker-wildfly 0 [OK]wildflyext/wildfly-camel WildFly with Camel Subsystem 0ianblenke/wildfly 0 [OK]arcamael/docker-wildfly 0 [OK]dmartin/wildfly 0 [OK]pires/wildfly-cluster-backend 0 [OK]aerogear/push-quickstarts-wildfly-dev 0 [OK]faga/wildfly Wildfly application server with ubuntu. 0abstractj/unifiedpush-wildfly AeroGear Wildfly Docker image 0murad/wildfly - oficial centos image - java JDK "1.8.0_0... 0aerogear/unifiedpush-wildfly-dev 0 [OK]ianblenke/wildfly-cluster 0 [OK]blackhm/wildfly 0khipu/wildfly8 0 [OK]rowanto/docker-wheezy-wildfly-java8 0 [OK]ordercloud/wildfly 0lavaliere/je-wildfly A Jenkins Enterprise demo master with a Wi... 0adorsys/wildfly Ubuntu - Wildfly - Base Image 0akalliya/wildfly 0lavaliere/joc-wildfly Jenkins Operations Center master with an a... 0tdiesler/wildfly 0apiman/on-wildfly8 0 [OK]rowanto/docker-wheezy-wildfly-java8-ex 0 [OK]arcamael/blog-wildfly 0lavaliere/wildfly 0jfaerman/wildfly 0yntelectual/wildfly 0svenvintges/wildfly 0dbrotsky/wildfly 0luksa/wildfly 0tdiesler/wildfly-camel 0blackhm/wildfly-junixsocket 0abstractj/unifiedpush-wildfly-dev AeroGear UnifiedPush server developer envi... 0abstractj/push-quickstarts-wildfly-dev AeroGear UnifiedPush Quickstarts developer... 0bn3t/wildfly-wicket-examples An image to run the wicket-examples on wil... 0lavaliere/wildfly-1 0munchee13/wildfly-node 0munchee13/wildfly-manager 0munchee13/wildfly-dandd 0munchee13/wildfly-admin 0bparees/wildfly-8-centos 0lecoz/wildflysiolapie fedora latest, jdk1.8.0_25, wildfly-8.1.0.... 0lecoz/wildflysshsiolapie wildfly 8.1.0.Final, jdk1.8.0_25, sshd, fe... 0wildflyext/example-camel-rest 0pepedigital/wildfly 0 [OK]tsuckow/wildfly JBoss Wildfly 8.1.0.Final standalone mode ... 0 [OK]mihahribar/wildfly Dockerfile for Wildfly running on Ubuntu 1... 0 [OK]hpehl/wildfly-domain Dockerfiles based on "jboss/wildfly" to se... 0 [OK]raynera/wildfly 0 [OK]hpehl/wildfly-standalone Dockerfile based on jboss/wildfly to setup... 0 [OK]aerogear/wildfly 0 [OK]piegsaj/wildfly 0 [OK]wildflyext/wildfly Tagged versions JBoss WildFly 0
Official images are taggedjboss/wildfly. - In order to push your own image, it needs to be built as a named image otherwise you’ll get an error as shown:
1232014/11/26 09:59:37 You cannot push a "root" repository. Please rename your repository in <user>/<repo> (ex: arungupta/wildfly-centos)
This can be easily done as shown:
12345678910111213141516171819202122232425262728293031323334353637383940414243444546474849505152535455wildfly-centos> docker build -t="arungupta/wildfly-centos" .Sending build context to Docker daemon 4.096 kBSending build context to Docker daemonStep 0 : FROM centos---> ae0c2d0bdc10Step 1 : MAINTAINER Arun Gupta <arungupta@redhat.com>---> Using cache---> e490dfcb3685Step 2 : RUN yum -y update && yum clean all---> Using cache---> f212cb9dbcf5Step 3 : RUN yum -y install xmlstarlet saxon augeas bsdtar unzip && yum clean all---> Using cache---> 28b11e6151f0Step 4 : RUN groupadd -r jboss -g 1000 && useradd -u 1000 -r -g jboss -m -d /opt/jboss -s /sbin/nologin -c "JBoss user" jboss---> Using cache---> 73603eab89b7Step 5 : WORKDIR /opt/jboss---> Using cache---> 9a661ae4341bStep 6 : USER jboss---> Using cache---> 6265153611c7Step 7 : USER root---> Using cache---> 12ed28a7acb7Step 8 : RUN yum -y install java-1.7.0-openjdk-devel && yum clean all---> Using cache---> 44c4bb92fa11Step 9 : USER jboss---> Using cache---> 930cb2a860f7Step 10 : ENV JAVA_HOME /usr/lib/jvm/java---> Using cache---> fff2c21b0a71Step 11 : ENV WILDFLY_VERSION 8.2.0.Final---> Using cache---> b7b7ca7a9172Step 12 : RUN cd $HOME && curl -O http://download.jboss.org/wildfly/$WILDFLY_VERSION/wildfly-$WILDFLY_VERSION.zip && unzip wildfly-$WILDFLY_VERSION.zip && mv $HOME/wildfly-$WILDFLY_VERSION $HOME/wildfly && rm wildfly-$WILDFLY_VERSION.zip---> Using cache---> a1bc79a43c77Step 13 : ENV JBOSS_HOME /opt/jboss/wildfly---> Using cache---> d46fdd618d55Step 14 : EXPOSE 8080 9990---> Running in 9c2c2a5ef41c---> 8988c8cbc051Removing intermediate container 9c2c2a5ef41cStep 15 : CMD /opt/jboss/wildfly/bin/standalone.sh -b 0.0.0.0---> Running in 9e28c3449ec1---> d989008d1f84Removing intermediate container 9e28c3449ec1Successfully built d989008d1f84
docker buildcommand builds the image,-tspecifies the repository name to be applied to the resulting image. - Once the image is built, it can be verified as:
12345678910111213wildfly-centos> docker imagesREPOSITORY TAG IMAGE ID CREATED VIRTUAL SIZEarungupta/wildfly-centos latest d989008d1f84 14 hours ago 619.6 MBwildfly-ubuntu latest a2e96e76eb10 43 hours ago 749.5 MB<none> <none> 0281986b0ed8 44 hours ago 749.5 MB<none> <none> 1a5e1aeadc85 44 hours ago 607.7 MBwildfly-centos latest 97c8780a7d6a 45 hours ago 619.6 MBregistry latest 7e2db37c6564 13 days ago 411.6 MBcentos latest ae0c2d0bdc10 3 weeks ago 224 MBjboss/wildfly latest 365390553f92 4 weeks ago 948.7 MBubuntu latest 5506de2b643b 4 weeks ago 199.3 MB
Notice the first line shows the named imagearungupta/wildfly-centos. - This image can then be pushed to Docker Hub as:
12345678910111213141516171819202122232425wildfly-centos> docker push arungupta/wildfly-centosThe push refers to a repository [arungupta/wildfly-centos] (len: 1)Sending image listPushing repository arungupta/wildfly-centos (1 tags)511136ea3c5a: Image already pushed, skipping5b12ef8fd570: Image already pushed, skippingae0c2d0bdc10: Image already pushed, skippinge490dfcb3685: Image successfully pushedf212cb9dbcf5: Image successfully pushed28b11e6151f0: Image successfully pushed73603eab89b7: Image successfully pushed9a661ae4341b: Image successfully pushed6265153611c7: Image successfully pushed12ed28a7acb7: Image successfully pushed44c4bb92fa11: Image successfully pushed930cb2a860f7: Image successfully pushedfff2c21b0a71: Image successfully pushedb7b7ca7a9172: Image successfully pusheda1bc79a43c77: Image successfully pushedd46fdd618d55: Image successfully pushed8988c8cbc051: Image successfully pushedd989008d1f84: Image successfully pushedPushing tag for rev [d989008d1f84] on {https://cdn-registry-1.docker.io/v1/repositories/arungupta/wildfly-centos/tags/latest} - And you can verify this by pulling the image:
1234567891011121314151617181920212223wildfly-centos> docker pull arungupta/wildfly-centosPulling repository arungupta/wildfly-centosd989008d1f84: Download complete511136ea3c5a: Download complete5b12ef8fd570: Download completeae0c2d0bdc10: Download completee490dfcb3685: Download completef212cb9dbcf5: Download complete28b11e6151f0: Download complete73603eab89b7: Download complete9a661ae4341b: Download complete6265153611c7: Download complete12ed28a7acb7: Download complete44c4bb92fa11: Download complete930cb2a860f7: Download completefff2c21b0a71: Download completeb7b7ca7a9172: Download completea1bc79a43c77: Download completed46fdd618d55: Download complete8988c8cbc051: Download completeStatus: Image is up to date for arungupta/wildfly-centos:latest
Enjoy!